Cyber Security Dynarose 薔薇靈動

Company Background
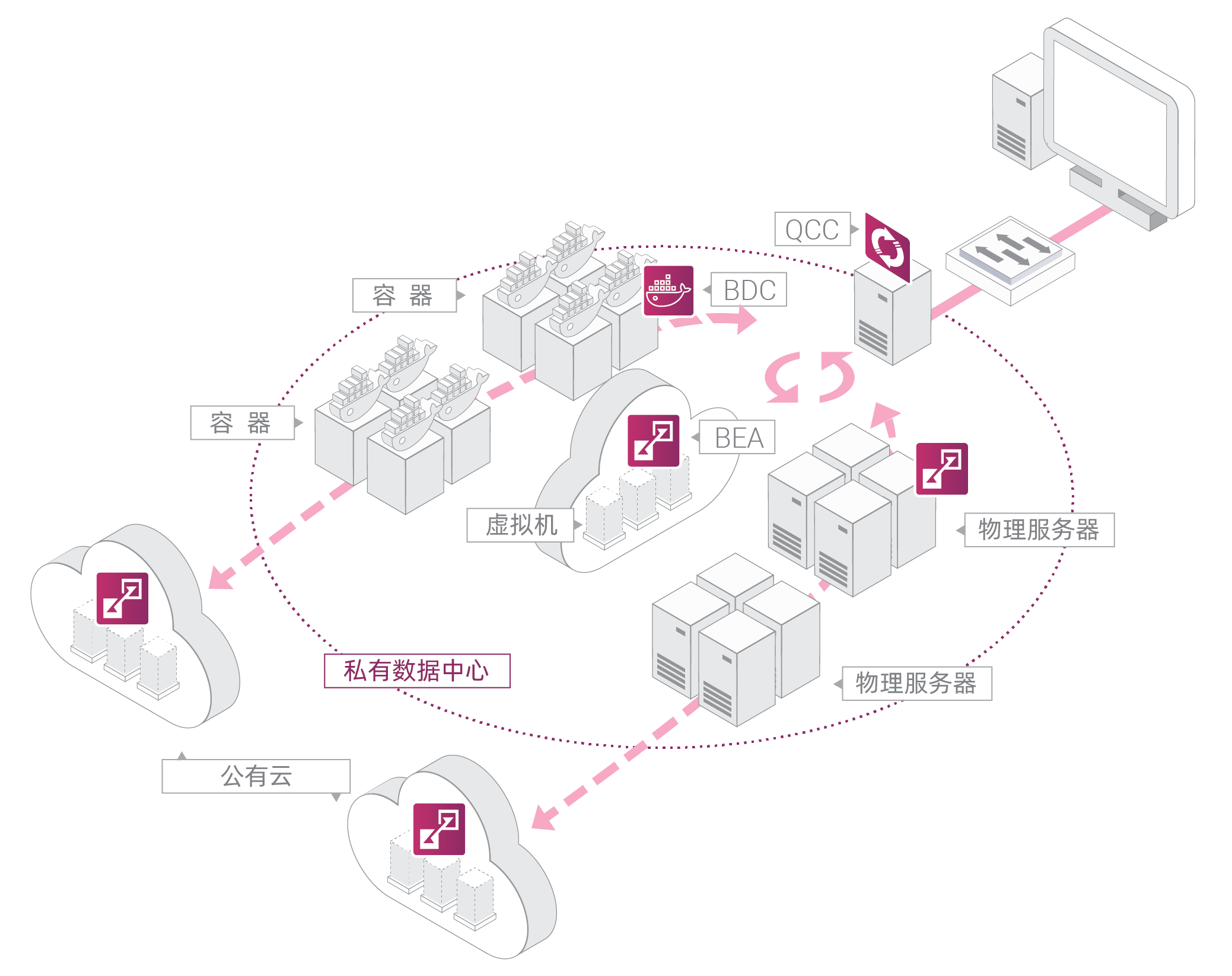
Dynarose is a leading provider of data center traffic micro-segmentation management solutions. Focused on advancing zero-trust micro-segmentation technology, Dynarose offers a unified security management platform tailored for data centers. It provides comprehensive visualization and fine-grained security policy control for both north-south user access and east-west service communication within enterprise data centers.
With eight years of deep technical expertise, Dynarose has resolved key industry challenges such as high cost, high complexity, and risk in micro-segmentation deployment. The technology enables organizations of all sizes to easily implement advanced internal network protection systems akin to those used by top-tier institutions.
Dynarose Key Differentiators and Strengths
- Unified platform managing both business user access and service-to-service calls within data centers.
- Comprehensive workload labeling and business connection visualization for effective resource management.
- Fine-grained east-west traffic access control combined with adaptive global policy computation.
- Smooth deployment of security policies with full-path application resource protection.
- Focus on network layer micro-segmentation that complements host-based system security.
- Awarded national high-tech enterprise status, and recognized as a leader in zero-trust security standards.
Target Markets & Applications
- Government agencies, financial institutions, energy sector, telecom operators, internet companies, and large enterprises.
- Internal data center traffic management and zero-trust network micro-segmentation.
Core Products
1. Zero Trust Workload Protection (微隔離)
- Purpose: Securing east-west traffic within data centers and cloud environments.
- Function: Enforces identity-based micro-segmentation between servers, containers, and workloads to prevent lateral movement by attackers.
2. Zero Trust Remote Access (零信任遠程訪問)
Purpose: Secure, remote access to internal applications for employees, partners, and contractors.
- Function: Replaces traditional VPNs by providing granular, least-privilege access to specific applications without exposing the entire network.
3. Zero Trust Application Access (零信任應用訪問)
Purpose: Securely publish internal business applications to external users without exposing them to the public internet.
- Function: Acts as a secure access proxy, making applications "dark" to everyone except authorized users.




 Cyber Security
Cyber Security Infrastructure
Infrastructure Networking
Networking Data Management
Data Management Work Productivity
Work Productivity Video Conference
Video Conference Business Intelligence
Business Intelligence


